Transferring the RDS Connection Broker and RD Web Access roles to another server.

In this article, we'll walk through the process of migrating (migration) the Remote Desktop Connection Broker and RDS Web Access roles to another server. This scenario can be used when you want to migrate RDS roles to a new version of Windows Server or when you need to migrate key RDS roles to other servers. In this example, we will migrate the RD Connection Broker role from Windows Server 2012 R2 to Windows Server 2019. We will also look at the specifics of migrating the RD Web Access role.
Some compatibility restrictions for Windows Server versions in an RDS farm:
- When upgrading from Windows Server, you must start with a host with the RD Connection Broker role;
If you are using the highly available RD Connection Broker role, then all you need to migrate is to leave one host with the Connection Broker role in the cluster, perform an in-place upgrade of the Windows Server version, then upgrade other servers and add them to the cluster.
- One terminal farm can contain RDSH hosts with different versions of Windows Server (2019/2016/2012R2). However, only servers with the same version of Windows Server can be in the same RDS collection. This means that you can make two RDS collections, for example, one with Windows Server 2019 hosts and one with Windows Server 2012 R2;
- Servers with previous versions of Windows server can use Connection Broker with newer version (i.e. RDSH hosts with WS2012R2 and WS2016 can use RD Connection Broker on WS2019, but not vice versa);
- When upgrading Windows Server on RDSH hosts, remember to install the RDS license server on the newer version and activate the new RDS CALs;
In our case, we have two RDS servers on Windows Server 2012 R2:
- Rds2 - with RD Connection Broker, Web Access and RDSH roles
- Rds1 - with RDSH role
The current distribution of roles in RDS can be displayed through Server Manager or using PowerShell:
Get-RDServer
Task: migrate all Connection Broker with configured RemoteApp and RDS collections to the new Windows Server 2019 (in-place upgrade is not applicable).
Prepare a new host with Windows Server 2019 and install the RD Connection Broker and RD Licensing roles (if needed) on it.
Windows Server does not have built-in tools to easily transfer configured RDS roles between servers.
To export/import the current RDCB settings, you can use the ExportImportRdsDeployment module from the PowerShell Gallery.
By default, RDCB uses the local SQL database (Windows Internal Database) to store settings, stored on the local disk of the RD Connection Broker server in the C:\Windows\rdcbDb\ directory.Install the ExportImportRdsDeployment module from the PowerShell Script Gallery (you can also install the PowerShell module offline):
Install-Module ExportImportRdsDeployment -Force
Import-Module ExportImportRdsDeployment
If Windows Management Framework 5.1 is not installed on Windows Server 2012 R2 (includes Windows PowerShell 5.1), the following error will appear when running the command:
Install-Module : The term 'Install-Module' is not recognized as the name of a cmdlet, function, script file, or operable program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again.Download and install KB3191564 ( https://www.microsoft.com/en-us/download/details.aspx?id=54616 ) to upgrade PowerShell to 5.1.
If you get an Install-Module: Unable to download from URI error when you run the command , you need to enable the use of TLS 1.2 for the connection:
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
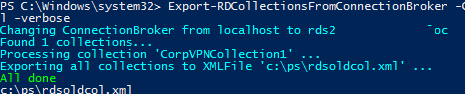
Export the RDS collection to an XML file:
Export-RDCollectionsFromConnectionBroker -ConnectionBroker localhost –XMLFile c:\ps\rdsoldcol.xml –verbose
Now you need to export your RDS configuration (including the list of servers in the deployment):
Export-RDDeploymentFromConnectionBroker -ConnectionBroker localhost –XMLFile c:\ps\rdsdeployment.xml -Verbose
If wildacard certificates are used on the old RDS server, you need to export them in pfx format (with password).
Copy both files to a new RDS server with Windows Server 2019. Also install the module:
Install-Module ExportImportRdsDeployment -Force
In this example, I am migrating an RDS configuration without certificates, so I specified non-existent files. If you use certificates in your RDS deployment, provide paths and passwords.
Now run the following commands:
$RDGatewayCertPath = "C:\\Temp\\noсert.pfx"
$RDWebAccessCertPath = "C:\\Temp\\noсert.pfx"
$RDRedirectorCertPath = "C:\\Temp\\noсert.pfx"
$RDPublishingCertPath = "C:\\Temp\\noсert.pfx "
$RDGatewayCertPassword = ConvertTo-SecureString -String "nopass" -AsPlainText -Force
$RDWebAccessCertPassword = ConvertTo-SecureString -String "nopass" -AsPlainText -Force
$RDRedirectorCertPassword = ConvertTo-SecureString -String "nopass" -AsPlainText -Force
$RDPublishingCertPassword = ConvertTo-SecureString -String "nopass" -AsPlainText -Force
Import-RDDeploymentToConnectionBroker -ConnectionBroker localhost -XmlFile c:\ps\rdsdeployment.xml -RDGatewayCertPath $RDGatewayCertPath -RDGatewayCertPassword $RDGatewayCertPassword -RDWebAccessCertPath $RDWebAccessCertPath -RDWebAccessCertPassword $RDWebAccessCertPassword -RDRedirectorCertPath $RDRedirectorCertPath -RDRedirectorCertPassword $RDRedirectorCertPassword -RDPublishingCertPath $RDPublishingCertPath -RDPublishingCertPassword $RDPublishingCertPassword -Verbose
If you do not use certificates for RDS, then a warning will appear in the script that the files were not found. Ignore this error.
Run the command Get-RDServer and verify that the RD Connection Broker role is now on the new server.
Import RDS collections:
Import-RDCollectionsToConnectionBroker -ConnectionBroker localhost -XmlFile "C:\PS\rdsoldcol.xml" -Verbose
Verify that all collections with configured rights and RemoteApps appear in the RDS Management Console.
Remove the RDCB role on the previous WS2012R2 host using Server Manager or the Remove-WindowsFeature command:
Remove-WindowsFeature RDS-Connection-Broker
There are nuances when migrating a customized RD Web Access Server role. If you are migrating the RDWebAccess role between different versions of Windows Server (with different versions of IIS), you must migrate the settings manually.
Install the RDS-Web-Access role and add a new server to your RDS farm:
Install-WindowsFeature RDS-Web-Access
Import certificates (if necessary).
Microsoft Web Deploy v3.6 can be used to migrate RDWeb site settings between servers running the same version of Windows Server.
Download and install the WebDeploy_amd64_en-US package (https://www.microsoft.com/en-us/download/details.aspx?id=43717) on both hosts.
To transfer site settings offline, you can use the following commands:
cd "C:\Program Files (x86)\IIS\Microsoft Web Deploy V3"On the original host:
msdeploy -verb:sync -source:apphostconfig="Default Web Site" -dest:archivedir=c:\ps\rdwebOn the target host:
msdeploy -verb:sync -source:archivedir=c:\ps\rdweb -dest:appHostConfig="Default Web Site"
You can also take advantage of IIS's backup capabilities.
Make sure your custom IIS settings are applied (including the change expired password form on RDS Web access ). Similarly, you can migrate the Remote Desktop Gateway role.
If your Web Access Server URL has changed, be sure to change it in the RDS SSO Transparent Authorization Policies.









Комментарии