How to Enable Two-Factor Authentication (2FA) for SSH on Linux?
In this article, we will show you how to enable two-factor authentication (2FA) for SSH login on Linux using Google PAM (Pluggable Authentication Module) and Microsoft Authenticator mobile app. 2FA allows you to add an extra security layer when you authenticate on a Linux host over SSH. After enabling 2FA, you will have to enter a one-time digital password (TOTP) from your smartphone in addition to your username and password (or RSA key) to SSH into Linux.
Install the Microsoft Authenticator mobile app on your smartphone (it is available both in Google Store and App Store).
Now you need to install and configure the Google PAM on your Linux host:
- Connect to your Linux host over SSH;
- Install the Google PAM Authenticator using your package manager:
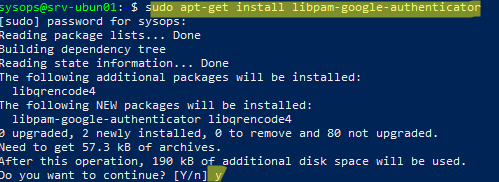
- Debian/Ubuntu:
sudo apt-get install libpam-google-authenticator - RHEL/CentOS/Fedora:
yum install google-authenticator
- Run the command:
google-authenticator - The tool will generate and display a QR code in the console:
- Run the Microsoft Authenticator app on your smartphone. Select Add account -> Personal account -> Scan a QR Code;
- Scan the QR code with the app. A new entry for your username and server will appear in the Authenticator app. You will use this item to get the one-time password to connect to your host;
- Note that a secret key and emergency codes are shown in your Linux console;
- Then google-authenticator shows some other questions:
- Do you want authentication tokens to be time-based?
Y -> Enter - Do you want me to update your “/home/sysops/.google_authenticator” file?
Y -> Enter - Do you want to disallow multiple uses of the same authentication token?
Y -> Enter
- Do you want to enable rate-limiting?
Y -> Enter
$ google-authenticator -t -f -d -w 3 -e 5 -r 3 -R 30-t – enables logon using one-time code
-f – saves the configuration to ~/.google_authenticator
-d – denies using previous codes
-w 3 – allows using one previous and one subsequent token (if time is not synchronized)
-e 5 – generates 5 emergency codes
-r 3 -R 30 – allows using no more than 3 logins every 30 seconds
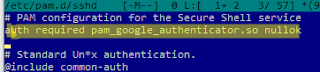
- Then add the following directive to /etc/pam.d/sshd:
auth required pam_google_authenticator.so nullok
- Then edit /etc/ssh/sshd_config:
sudo mcedit /etc/ssh/sshd_config - Change the
ChallengeResponseAuthenticationvalue toYes:
ChallengeResponseAuthentication yes
- Save the changes in sshd_config and restart sshd:
service ssh restart
- By default, tokens are good for 30 seconds…
Y -> Enter
Then try to connect to your Linux host over SSH. You will be asked to enter a verification code before entering a password.
Open the Authenticator app on your smartphone and find the user of your Linux host. Enter a 6-character one-time password code that the Authenticator generated for you into the console.
Note that the one-time password code is valid for a limited time (30 seconds by default). If you have entered the correct code, you will be prompted to enter your Linux user password.
If the logon is successful, the following line appears in the authentication log:
cat /var/log/auth.log
Jul 20 11:12:22 srvubun01 sshd(pam_google_authenticator)[6242]: Accepted google_authenticator for sysops
If the incorrect code is entered, the log shows errors:
Jul 20 11:14:20 srvubun01 sshd(pam_google_authenticator)[6436]: Invalid verification code for sysops Jul 20 11:14:22 srvubun01 sshd[6436]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.10.15 user=sysops
If you want to use 2FA together with the SSH key authentication, add the following directives to /etc/ssh/sshd_config:
PasswordAuthentication no PubkeyAuthentication yes AuthenticationMethods publickey,keyboard-interactive









Комментарии