We get the history of program launches in Windows using audit policies.

In this article, we will look at how you can use Windows audit policies to find out which programs were running on a computer. Quite often, the administrator is required to provide information about what applications the user runs, when he last ran the application, and so on. This information can be gathered from the Windows event log and converted into a handy report using PowerShell.
- The first step is to enable the process start/stop audit policy in Windows.Open the local group policy editor gpedit.msc;
If you want to enable the process audit policy on computers in an Active Directory domain, you need to use the domain GPO editor - gpmc.msc.
- Go to GPO Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Audit Policy;
- Enable the Audit process tracking policy and the event type Success;
- Save the changes and update the local policies on the client with the command: gpupdate /force
Open the Event Viewer ( eventvwr.msc ) and expand the Windows Logs -> Security section. Now, when any program (process) starts, the Process Creation event with EventID 4688 appears in this event log.
A new process has been created.
The event information includes the user who launched the program ( Creator Subject ), the name of the process's executable file ( New Process Name ), and the parent process from which the application was launched (Creator Process Name).
The process exit event (A process has exited) has EventID 4689.
Please note that when you enable the Audit process tracking policy discussed above , all process-related events begin to be stored in the Security log. If you want to reduce the number of events in the Event Viewer and store only information about startup events, you can disable this policy and enable only the Audit Process Creation advanced audit policy (Windows Settings -> Security Settings -> Advanced Audit Policy Configurations -> System Audit Policy -> detailed tracking).
To include information about process startup parameters (arguments with which programs are launched) in audit events, also enable the Include command line in process creation events GPO option in Computer Configuration -> Administrative Templates -> System -> Audit Process Creation.
After you enable this policy, you can see in the Process Command Line argument with which argument a particular process was launched.
Don't forget to increase the size of the Security log from the default 20 MB. This will allow you to store the application launch history for a longer period. To do this, open the properties of the Security log and increase the value of the Maximum log size parameter.
You can use the Event Viewer filters to analyze programs launched by the user. But this is not very convenient. Below I will show some PowerShell scripts that will allow you to get convenient lists with the history of applications launched by users.
$processhistory = @()
$today = get-date -DisplayHint date -UFormat %Y-%m-%d
$events=Get-WinEvent -FilterHashtable @{
LogName = 'Security'
starttime="$today"
ID = 4688
}
foreach ($event in $events){
$proc = New-Object PSObject -Property @{
ProcessName=$event.Properties[5].Value
Time=$event.TimeCreated
CommandLine=$event.Properties[8].Value
User=$event.Properties[1].Value
ParentProcess=$event.Properties[13].Value
}
$processhistory += $proc
}
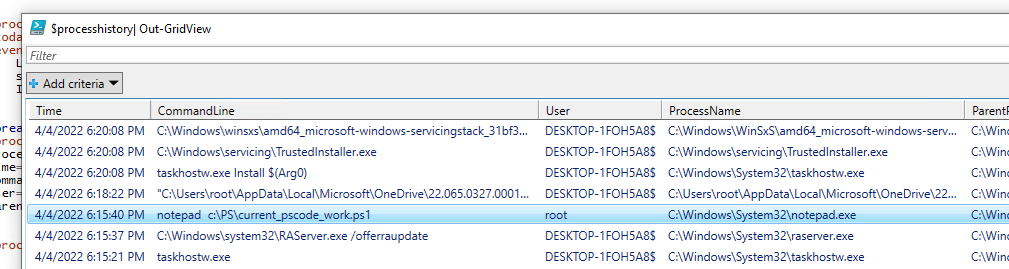
$processhistory| Out-GridView
This PowerShell script will select all program launch events for today and display a list of processes, startup times, and users in an Out-GridView graphical table.
With PowerShell, you can manage processes in Windows.The resulting array of objects can be used to perform various queries.
- For example,Find all users who have run a specific application:
$proc_name=”notepad++.exe”
$processhistory | where-object {$_.ProcessName –like “*$proc_name*”}|out-gridview
- Display a list of programs that a specific user has launched today:
$username="aivanov"
$processhistory | where-object {$_.User –like “*$username*”}|out-gridview
Such scripts are often used to analyze the launch of user programs on the farm's RDS servers.
Also, the history of running programs in Windows is kept in the file %SystemRoot%\AppCompat\Programs\ Amcache.hve. The file is locked by Windows and can only be read by booting from a LiveCD or a boot/install disk. The file contains launch marks, program installation/removal marks, checksums of the executable file (SHA1). To convert this binary file to text format, you need to use third-party utilities (for example, regripper).
I also remind you that PowerShell also maintains its own history of running commands.










Комментарии